In this post we will do the BlueTeamLabs’ Deep Blue lab. Doing these labs that are associated to a specific tool is a good way to test out available tools so you can find the best to have in your arsenal.
Scenario
A Windows workstation was recently compromised, and evidence suggests it was an attack against internet-facing RDP, then Meterpreter was deployed to conduct ‘Actions on Objectives’. Can you verify these findings?
You have been provided with the Security.evtx and System.evtx log exports from the compromised system - you should analyze these, NOT the Windows logs generated by the lab machine (when using DeepBlueCLI ensure you’re providing the path to these files, stored inside \Desktop\Investigation\.
Reading Material:
https://github.com/sans-blue-team/DeepBlueCLI
Time for class
What are EVTX logs?
In Windows systems (as of Windows Vista) audit events are saved to files with extension .evtx (Windows XML Event Log), and are typically stored in C:\Windows\System32\winevt\Logs location. This new format called Windows XML Event Log (EVTX) format superseeds the EVT format used in Windows XP.
Windows EVTX files are stored in a binary format with several advantages:
- Rollover. When the event log fills up, events simply rotate into the start of the file overwriting older events. This allows the file size to be limited.
- Binary XML format provides some compression. Not as much compression as
gziporbzip, however EVTX files use a binary encoding to save some space over plain XML. - Structured records with strong types. Structured logs allow for accurate and fast filtering of log files, and remove the need to parse unstructured text.
As the log files are saved in binary XML format, we need specialized libraries to open and convert them to readable format.
The simplest way is to use Windows’ default tool - “Event Viewer” - and select the log we are interested in analyzing.
What are Security.evtx and System.evtx logs?
In an investigation we are limited in time, so we cannot go over every log file there is.
Among others, the Security.evtx and System.evtx files are a good baseline to start our investigation since they are two of the main Windows event logs.
In the table below there are some examples of interesting artifacts we can find in each of these logs.
| Log file name | What information it provides |
|---|---|
System.evtx |
- Audit log clearing - Services installation/execution/modification |
Security.evtx |
- Modifications in account/groups - Audit log clearing - Windows firewall connections - User logons - Process creation - Creation/Deletion/Modification of Scheduled tasks - Services installation |
What is DeepBlue tool?
DeepBlueCLI is a PowerShell module for Threat Hunting via Windows Event Logs, created by Eric Conrad, and is a part of SANS’ suggested cyber security tools.
If no tool is used, you have to know which Event IDs specifically you want to search for. A basic knowledge of relevant Event IDs is important, but tools like these help us quickly parse the logs and have some insights right away.
Usage
cd <path-to>\DeepBlueCLI-master
powershell
Set-ExecutionPolicy Bypass # this may be needed to be able to run the tool
.\DeepBlue.ps1 <file>.evtx
Lab Questions
1. Which user account ran GoogleUpdate.exe? (4 points)
“Using DeepBlueCLI, investigate the recovered Security log (Security.evtx).”
To use the tool on that log let’s do:
.\DeepBlue.ps1 C:\Users\BTLOTest\Desktop\Investigation\Security.evtx
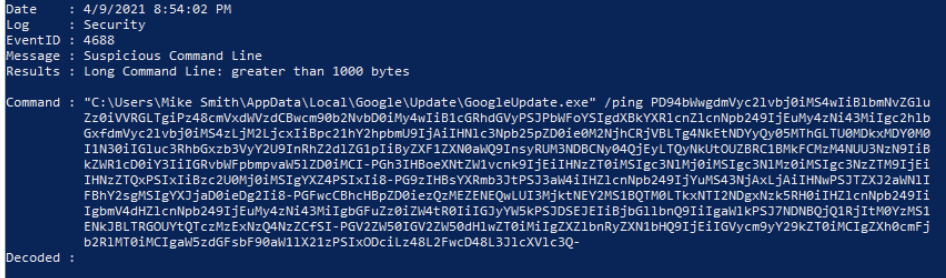
We can see that suspicious GoogleUpdate.exe was run under the account “Mike Smith”.
✔️ Mike Smith
2. At what time is there likely evidence of Meterpreter activity? (4 points)
“Using DeepBlueCLI investigate the recovered Security.evtx log.”
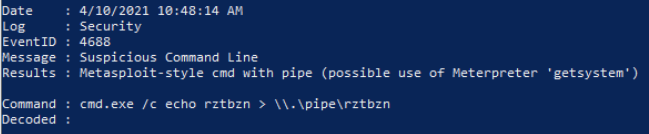
✔️ 4/10/2021 10:48:14
3. What is the name of the suspicious service created? (5 points)
“Using DeepBlueCLI investigate the recovered System.evtx log.”
.\DeepBlue.ps1 C:\Users\BTLOTest\Desktop\Investigation\System.evtx
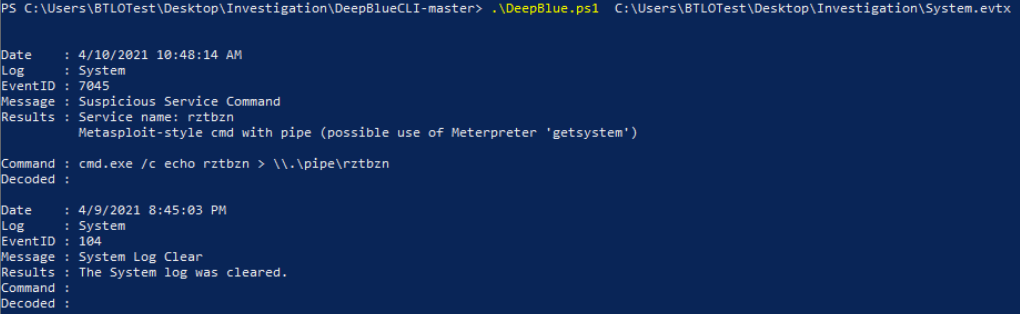
✔️ rztbzn
4. Identify the malicious executable downloaded that was used to gain a Meterpreter reverse shell. (4 points)
“Investigate the Security.evtx log in Event Viewer. Process creation is being audited (event ID 4688). This happened between 10:30 and 10:50 AM on the 10th of April 2021”
Looking at the answer of question 2., we observed Meterpreter activity at 4/10/2021 10:48:14. As such we need to start look to our logs exactly before that time.
Indeed, at 4/10/2021 10:46:55, approximately 1min before Meterpreter activity, we can see a download of an executable with a pretty ambiguous name on the users’ Download folder (image below).
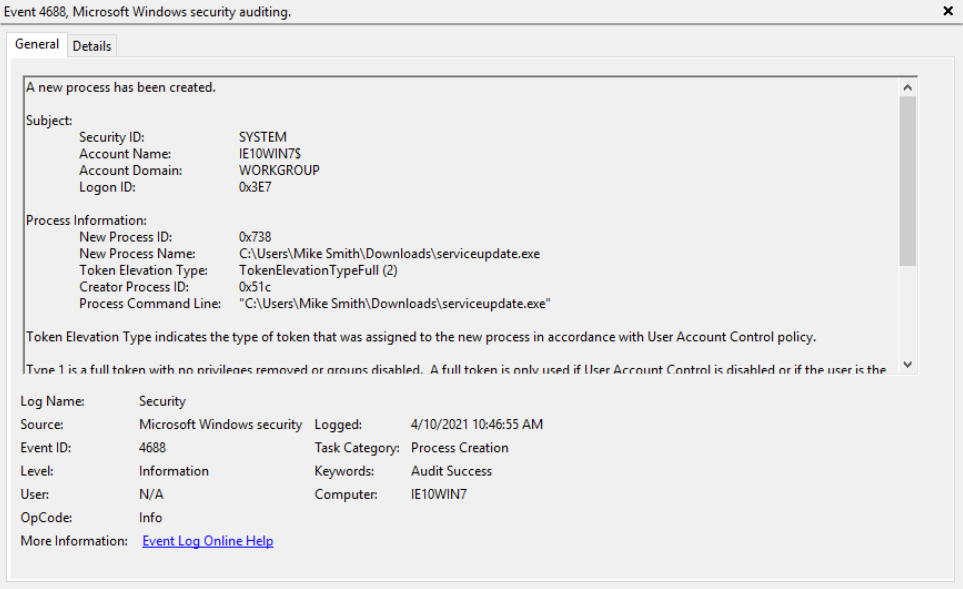
✔️ Mike Smith, serviceupdate.exe
5. What was the account created by the attacker to obtain persistence? (4 points)
“It’s also believed that an additional account was created to ensure persistence between 11:25 AM and 11:40 AM on the 10th April 2021. What was the command line used to create this account? (Make sure you’ve found the right account!)”
When searching for account creation, one common command I always look for is net user.
Looking for this command, there are a couple of users that were added. However, one of them - ServiceAct - is followed by being added to Administrators and Remote Desktop Users groups, which rings all the bells!
Note: In a digital forensics report, all added users should be presented.
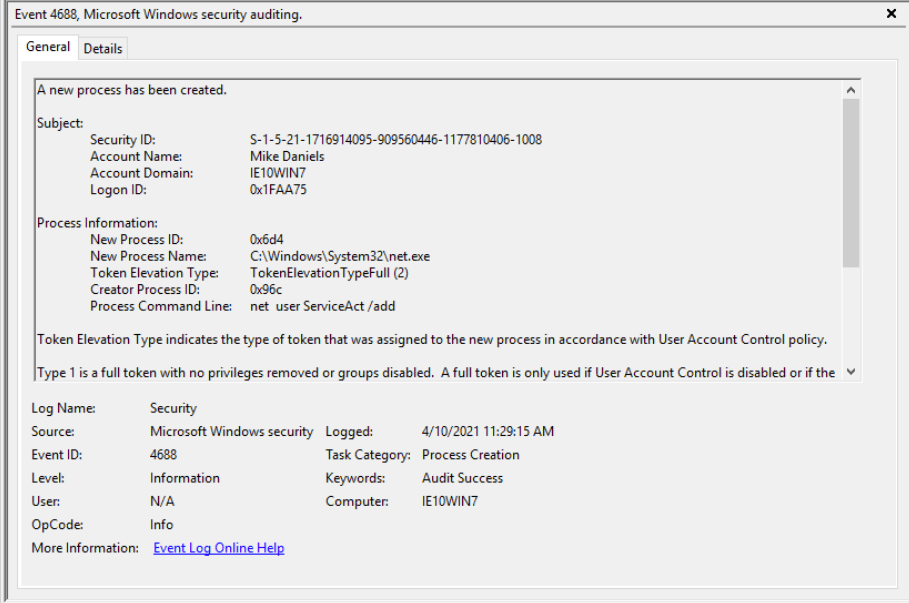
✔️ net user ServiceAct /add
6. What two local groups was this new account added to? (4 points)
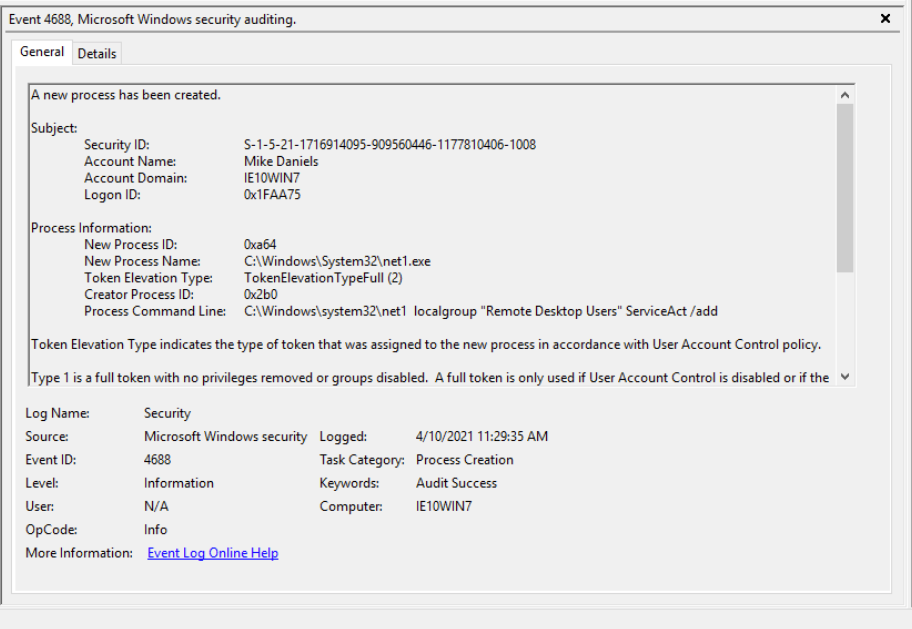
✔️ Administrators, Remote Desktop Users
And voilá!
Happy Hunting 🕵️♀️